🚀 Release Note — IPv4 Threat Intelligence Search Page
We are excited to announce a new feature in OneFirewall Alliance Ltd, our threat intelligence sharing platform.This release introduces a dedicated IPv4 Threat Intelligence Search Page that provides comprehensive visibility into malicious activities associated with any IPv4 address.
🔎 New Functionalities
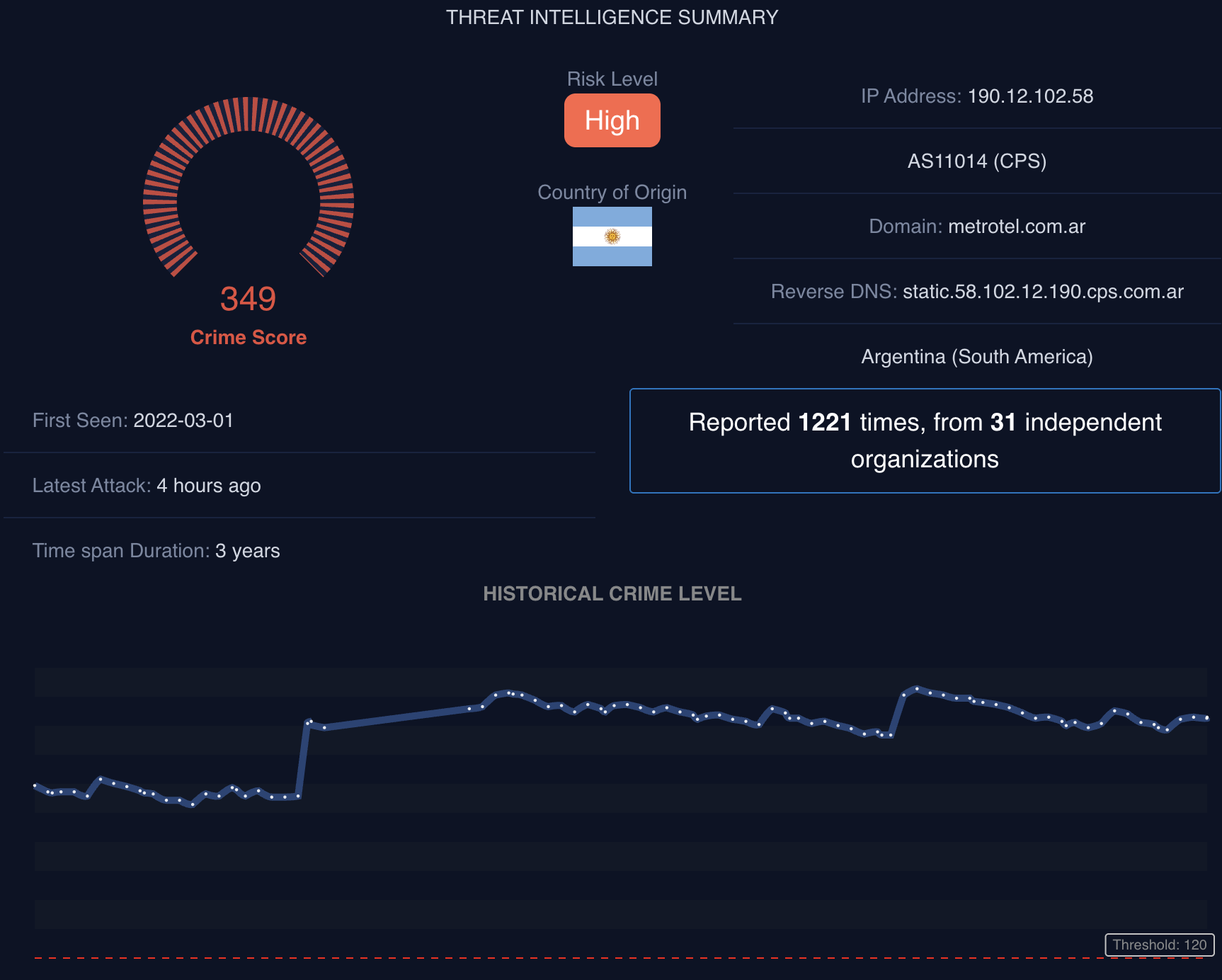
1. IPv4 Threat Intelligence Summary
- Query any IPv4 address to retrieve detailed intelligence data.
- Key indicators displayed include:
- Risk Level (with Crime Score visualization).
- IP Address details: ASN, domain, reverse DNS, country of origin.
- Timeline insights:
- First Seen date
- Latest Attack timestamp
- Time span duration of malicious activity
- Community intelligence: number of reports and distinct contributing organizations.
- Historical Crime Level Graph visualizes malicious activity trends over time.
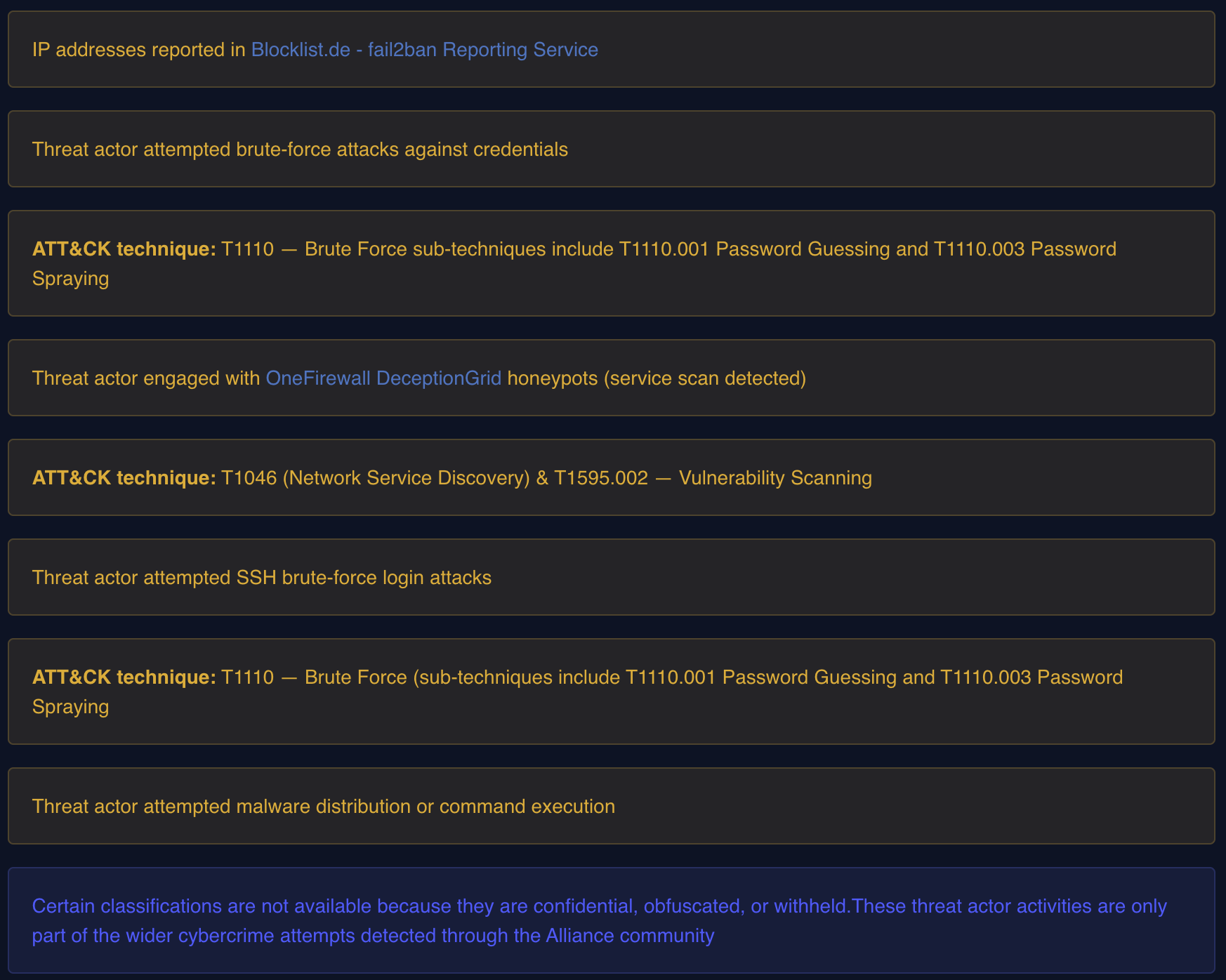
2. Detailed Threat Activity Feed
- Displays enriched threat intelligence events tied to the IP address.
- Each entry provides:
- Human-readable description of the threat actor activity (e.g., brute-force attempts, malware distribution, reconnaissance).
- Mapped MITRE ATT&CK Techniques for standardized classification of adversary behavior.
- Honeypot engagement logs from OneFirewall DeceptionGrid.
- External references (e.g., Blocklist.de reports).
3. Contextual Intelligence Notes
- Explanations on why certain classifications may not be available (e.g., confidential, obfuscated, or withheld).
- Clarifies that the reported activities represent a subset of broader cybercrime attempts identified by the Alliance community.
🎯 Benefits
- Faster threat attribution: immediate context on malicious IPv4 activity.
- Community-driven intelligence: aggregated reports from multiple independent organizations.
- Operational value: supports SOC analysts, incident responders, and threat hunters in making data-driven security decisions.
- Standardized language: leveraging MITRE ATT&CK ensures consistent classification across reports.

