Purpose
This guide explains how to ingest OneFirewall Alliance IP feeds into a Palo Alto firewall using External Dynamic Lists (EDL), with a secure proxy method to support Bearer Token authentication.Requirements
Ensure you’re using PAN‑OS 10.0+, which supports HTTPS-based EDLs and certificate profiles.Step 1: Generate API Token
- Log into your OneFirewall Alliance profile.
- Navigate to the API Access section.
- Generate a JWT token.
- Save this token securely — it will be used for authenticating feed requests.
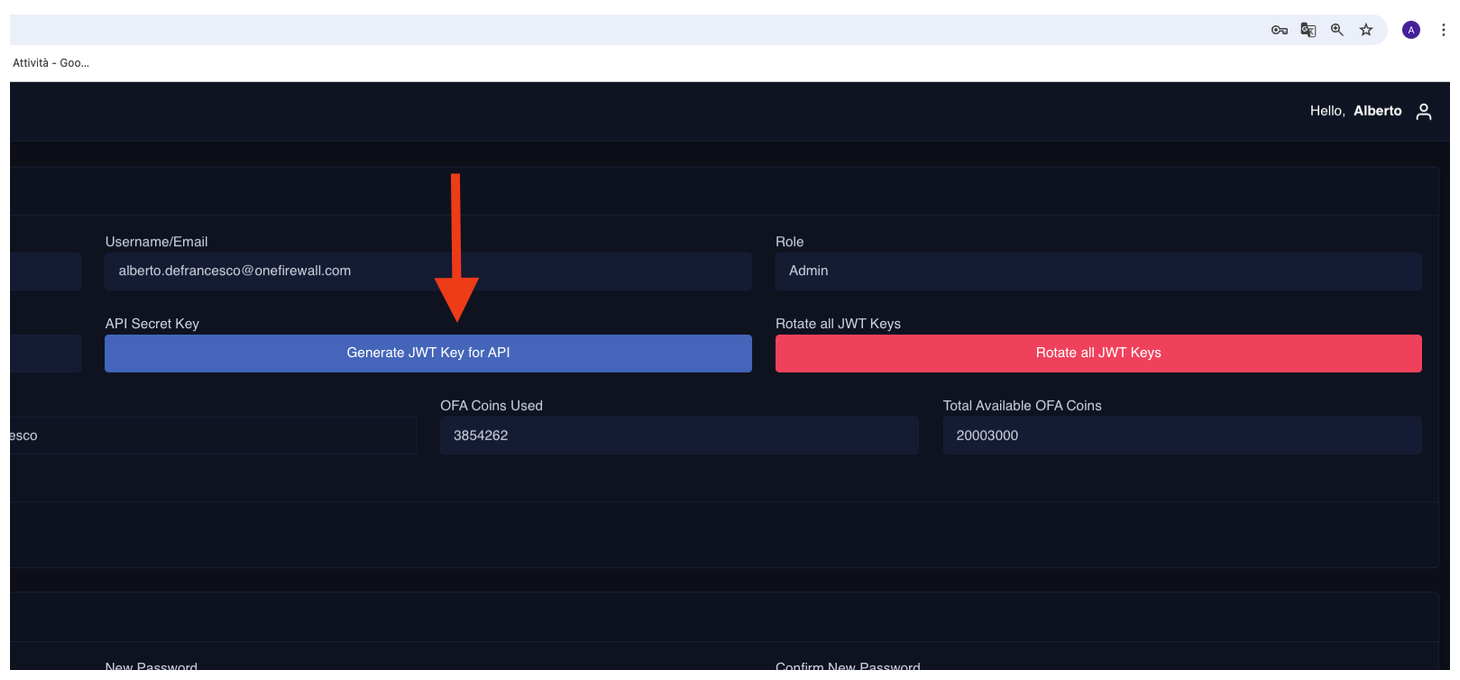
3. Create the External Dynamic List (EDL)
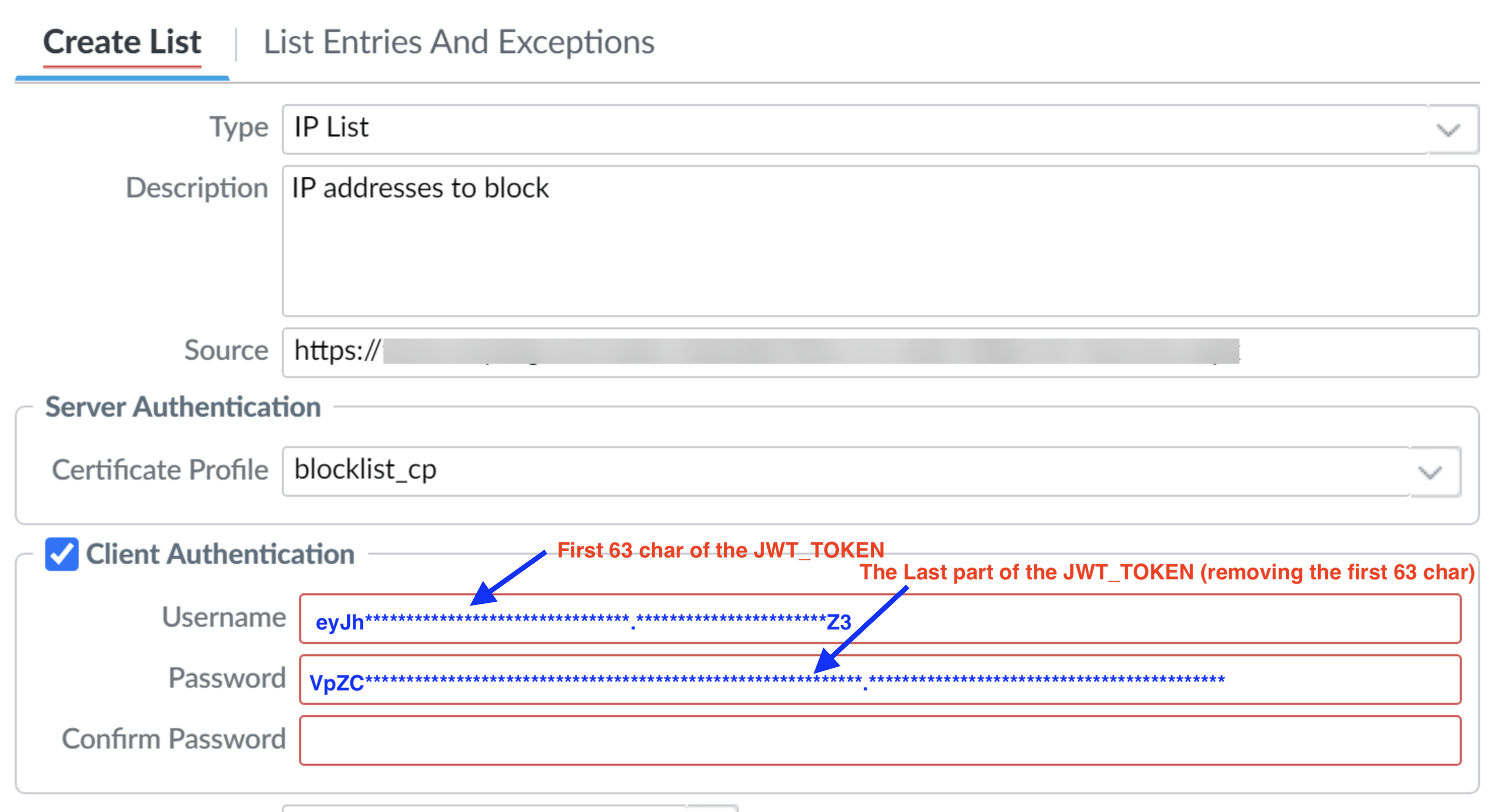
- In the Palo Alto Web UI, go to Objects → External Dynamic Lists.
- Click Add.
-
Fill in the fields:
-
Name:
onefirewall_ipv4_feed -
Type:
IP List -
Source:
If the Client Authentication appears like in figure, you can also put basic auth in the required section and the source will be like the following:the credentials should be like explained in the figure. If the Client Authentication is not present, you can pass credentials like in the following section: - Recurring: Every 15 minutes (or as needed)
- Certificate Profile: (optional, only needed for HTTPS with custom certs)
-
Name:
- Click OK and then Commit your changes.
4. Apply the EDL in a Security Policy
- Go to Policies → Security.
-
Create a new rule or edit an existing one:
- Source / Destination Zone: According to your environment
- Destination Address: Add an address object referencing the EDL (
onefirewall_ipv4_feed) - Action:
DenyorDrop
- Name and place the rule in the correct policy order.
- Commit the configuration.

