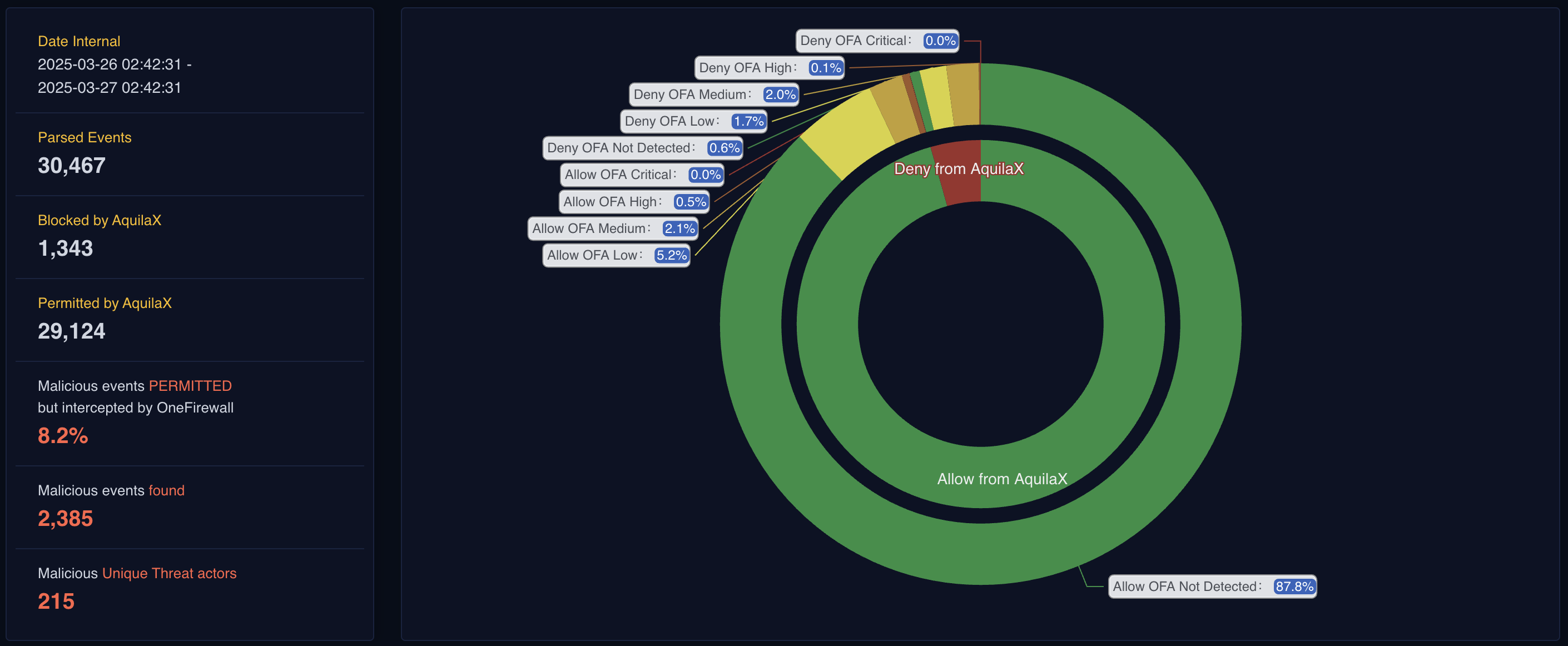
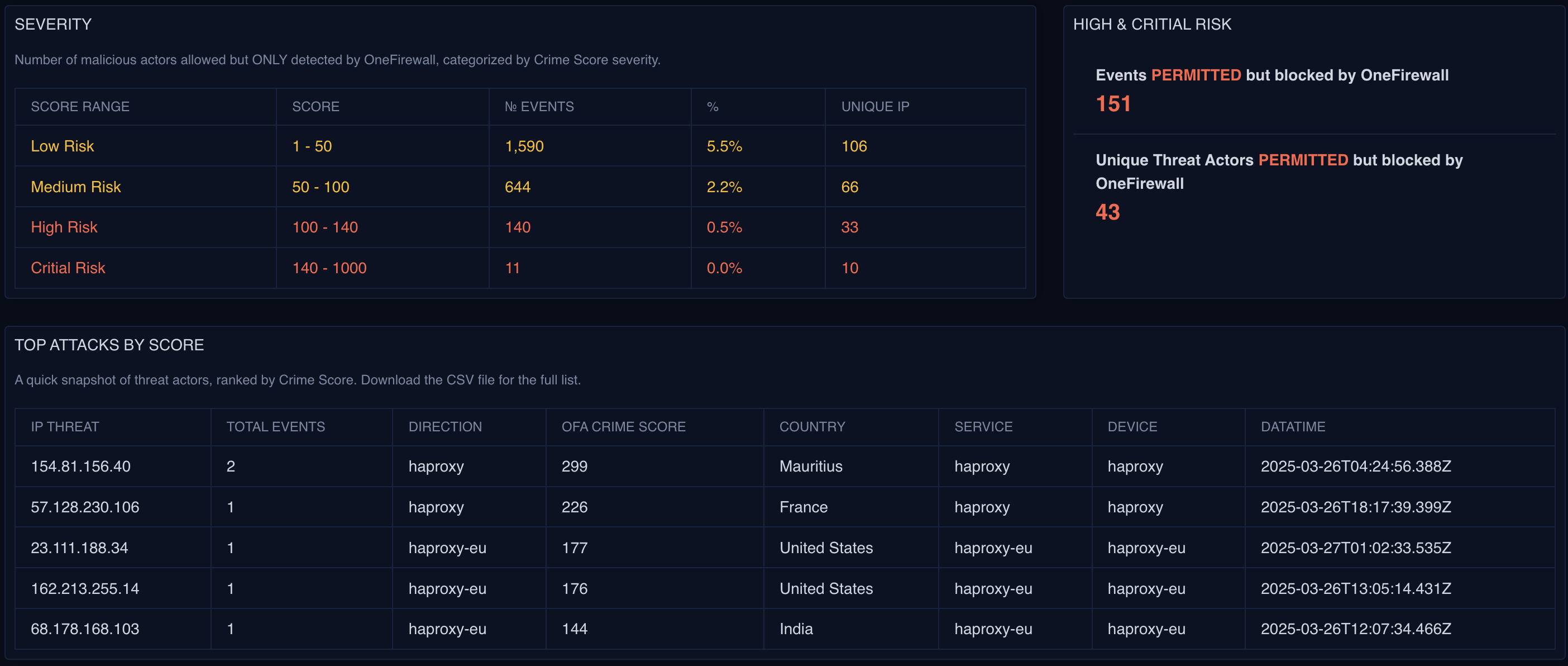
OneFirewall leverages proprietary threat intelligence from its Cybersecurity Alliance to detect previously allowed traffic that has since been identified as malicious.
🔐 Getting Started
To begin using NetFlow Security Analysis, follow the steps below:1. Account and Licensing
- Ensure you have an active OneFirewall account (on-prem or cloud).
- Verify that your account includes:
- A valid license for NetFlow Security Analysis.
- Proper permissions to access API functionalities.
2. Generate Your API Token
Once you have access:- Navigate to your profile settings on the OneFirewall platform.
- Generate an API token which will be used to authorize your requests.
📡 Sending Network Metadata
To send traffic data for analysis, use the following API endpoint:POST Request
- firewall: Name of your firewall or IPS
- direction:
inboundoroutbound - src_ip / dst_ip: Source and destination IPv4 addresses
- src_port / dst_port: Source and destination port numbers
- service: Human-readable name of the service
- action:
AlloworDeny
Response Codes
- 200 OK – Request accepted
- 201 Created – Resource created and queued for analysis
- 4xx – Error in request (e.g., malformed payload or invalid token)
⏱️ Rate Limiting
You can send multiple requests, but be aware of the following limits:- 🔄 150 requests per 10 seconds
- Requests beyond this rate will be throttled or rejected
📊 View Live Reports
After sending the traffic metadata, you can monitor results live:- Go to https://app.onefirewall.com
- Navigate to the Live section
- View real-time analysis and threat assessments
🧠 Why Use OneFirewall?
According to the OneFirewall Value Proposition Report, NetFlow Security Analysis helps your organization:- ✅ Detect malicious activity that slipped past traditional security layers
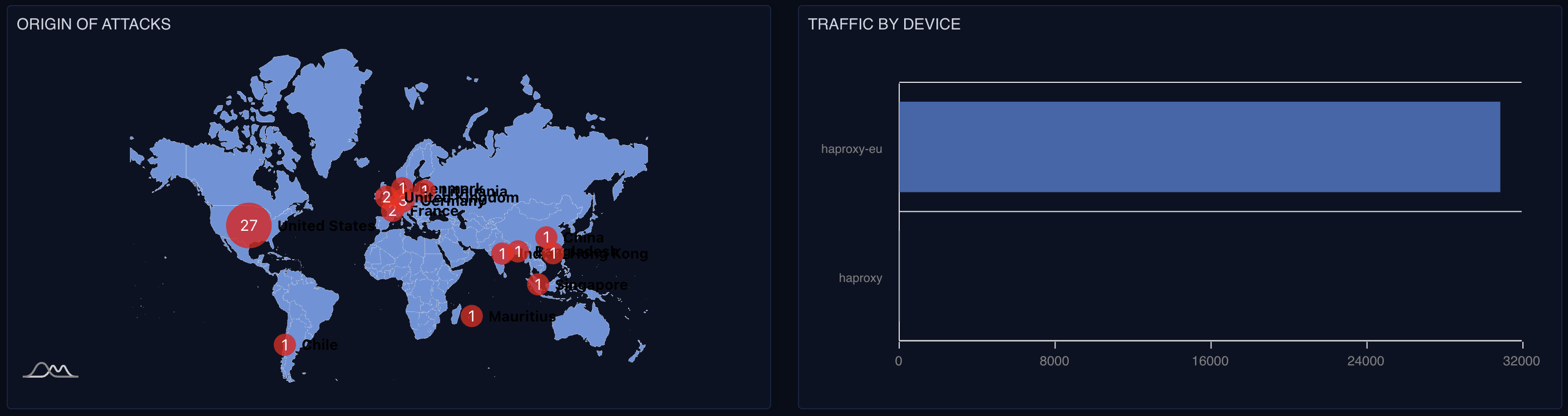
- ✅ Gain visibility into blocked and allowed traffic across your perimeter
- ✅ Leverage global threat intelligence from the Cybersecurity Alliance
- ✅ Strengthen your zero-trust strategy with data-driven insights

